Zero Trust Security: A New Paradigm for Modern Cybersecurity
In today’s interconnected world, the traditional cybersecurity model of perimeter defense is no longer sufficient to protect organizations from advanced cyber threats. The rise of remote work, cloud computing, and the growing complexity of IT environments has necessitated a shift towards a more robust and adaptable approach to security. This is where “Zero Trust Security” steps in to revolutionize the way we think about safeguarding our digital assets.

What is Zero Trust Security?
Zero Trust is a cybersecurity framework built on the fundamental principle of never trusting and always verifying. Unlike the traditional “castle-and-moat” model, where once you’re inside the network, you’re considered trusted, Zero Trust assumes that threats could be both external and internal. It demands continuous verification of any entity trying to access resources within the network, regardless of their location.
The Zero Trust Principles
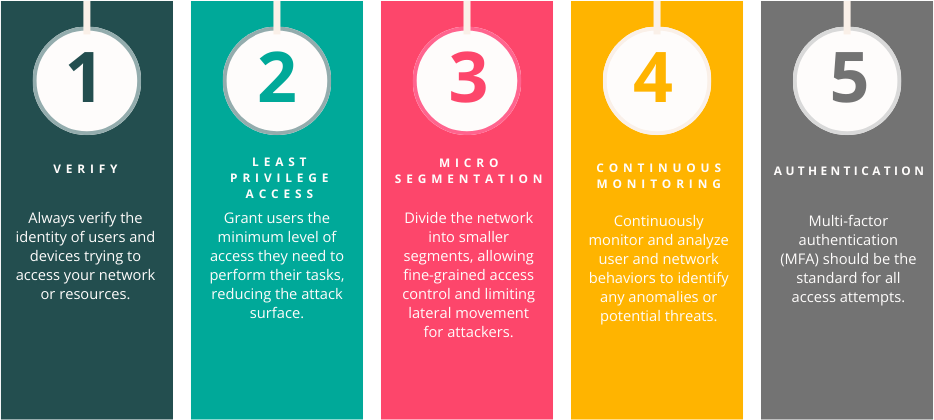
Zero Trust relies on several core principles:
Real-World Scenarios: How Zero Trust Works
Scenario 1: Remote Employee Access
Consider a scenario where a remote employee wants to access sensitive corporate data from a personal device. In a Zero Trust environment, the user must first authenticate using strong multi-factor authentication (MFA). The system continuously monitors their behavior and the device’s security posture. If any anomalies are detected, access may be restricted or further verified.
Scenario 2: Third-Party Vendor Access
Imagine a third-party vendor requires access to a particular system for maintenance. Under Zero Trust, the vendor’s identity is verified, and their access is restricted to the specific resources required for the task. After the task is complete, access is revoked.
The Advantages of Zero Trust Security
Zero Trust Security offers several benefits:
- Improved Security: By continuously verifying identities and monitoring for unusual behavior, Zero Trust reduces the risk of data breaches.
- Reduced Attack Surface: Least privilege access and micro-segmentation limit the potential points of attack.
- Adaptability: It’s designed to work in modern, dynamic environments, including remote work and cloud services.
Challenges and Considerations
Implementing Zero Trust is not without its challenges. It can be complex to set up and requires a cultural shift within an organization. Additionally, there may be a need for investment in robust identity and access management solutions.
Conclusion
In an era where the threat landscape is constantly evolving, a Zero Trust Security model is a proactive and effective approach to safeguarding your organization’s digital assets. By adopting this framework, organizations can stay ahead of the curve, ensuring the protection of sensitive data and maintaining a strong security posture.
Zero Trust is more than just a buzzword; it’s a strategic approach that enhances cybersecurity and adapts to the dynamic nature of the modern digital landscape. Embracing the Zero Trust model today could be the key to a more secure and resilient future.


