SOC 2 Audit: The gold standard for data security
In today’s rapidly evolving digital landscape, trust is the foundation upon which successful businesses are built. Customers, partners, and stakeholders demand assurance that their sensitive data is handled securely and that the systems and processes in place to protect it are both designed effectively and operating as intended.
This is where SOC 2 Audit services come into play, offering comprehensive reports that attest to the suitability, design, and operating effectiveness of controls.
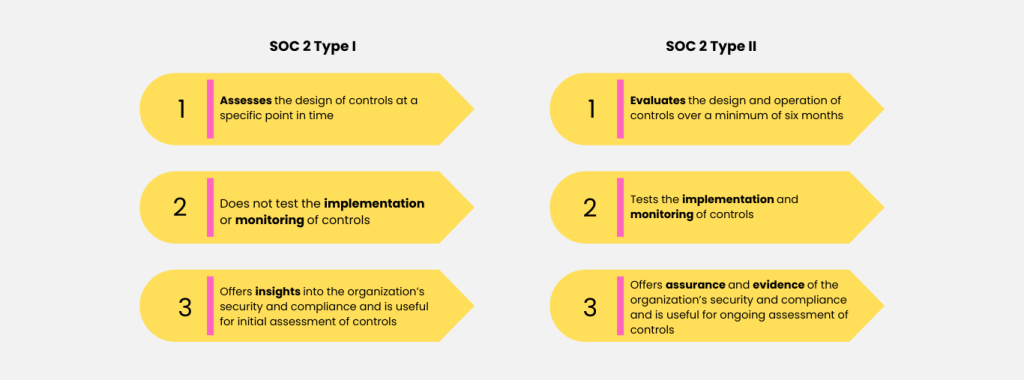
The SOC 2 Type I report showcases service suitability at a specific date, but does not assess effectiveness. In contrast, the impressive SOC 2 Type II report demonstrates effective management for a minimum of 6 (six) months, providing solid evidence of their suitability.