Step 1 - Initiate a Comprehensive Evaluation
Step 2 - Identify Organizational Cybersecurity Risks
Step 3 - Develop a Cybersecurity Risk Management Plan
Step 4 - Apply Cybersecurity Controls
Step 5 - Establish Detection and Response Capabilities
Step 6 - Create a Resilient Cybersecurity Recovery Plan
Step 7 - Monitor and Evaluate the Effectiveness
Step 8 - Continuous Improvement
Step 1 - Initiate a Comprehensive Evaluation
Step 1 – Initiate a Comprehensive Evaluation
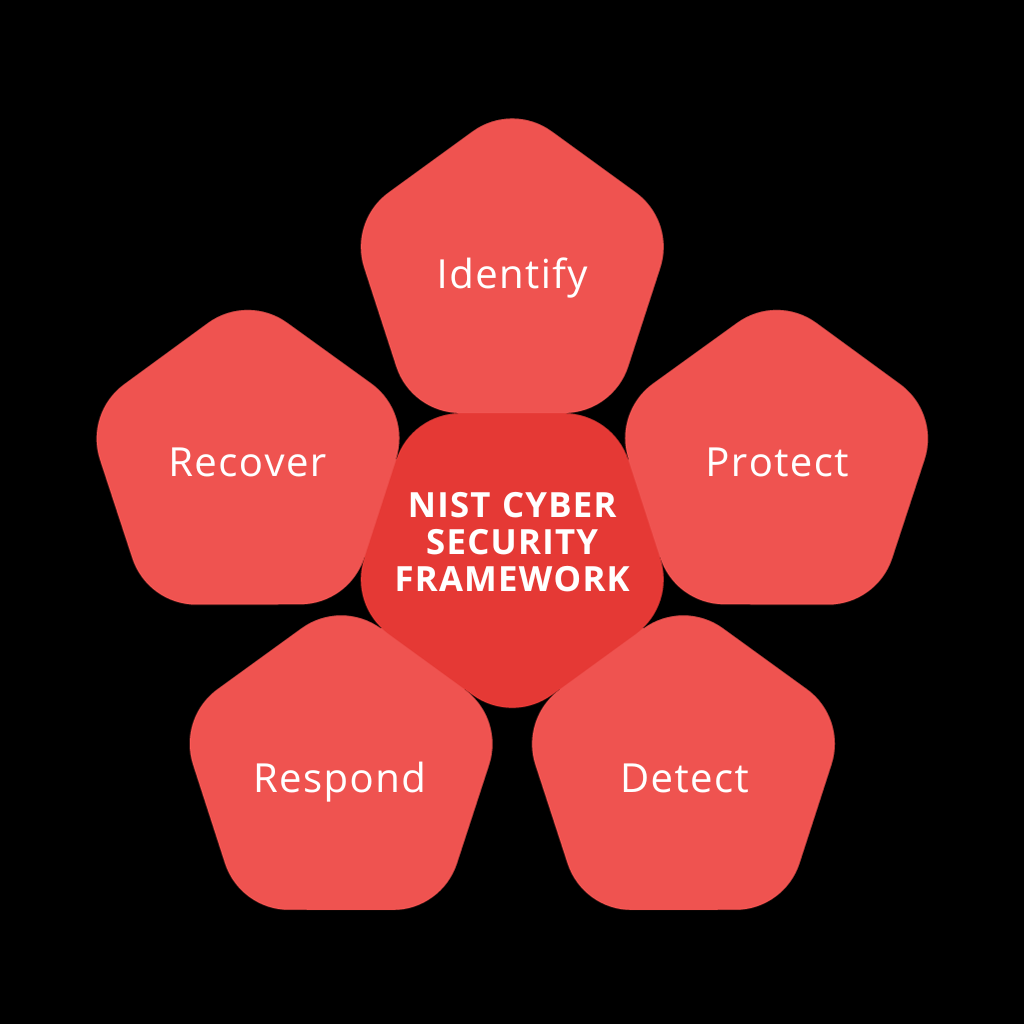
Embarking on the implementation of the NIST CSF commences with a profound understanding of its intricate components and their interconnections. At its core, this framework encompasses five paramount functions – Identity, Protect, Detect, Respond, and Recover – all of which play a pivotal role in effectively managing the multifaceted realm of cybersecurity risks.
Step 2 - Identify Organizational Cybersecurity Risks
Step 2 – Identify Organizational Cybersecurity Risks
Within the context of the NIST CSF, the imperative first step involves discerning the cybersecurity risks prevalent within an organization. This encompasses a comprehensive identification of the systems, assets, data, and capabilities that lie at the very heart of the organization’s operations. A meticulous risk assessment exercise is conducted to accurately identify potential threats and vulnerabilities that may jeopardize its integrity.
Step 3 - Develop a Cybersecurity Risk Management Plan
Step 3 – Develop a Cybersecurity Risk Management Plan
Drawing from the results of the risk assessment, an elaborate and tailored plan for cybersecurity risk management emerges. This meticulously crafted plan encompasses a repertoire of strategies and actions that are specifically designed to address the identified risks. Crucially, the plan is astutely aligned with the organization’s overarching business objectives, risk tolerance, and the resources at its disposal.
Step 4 - Apply Cybersecurity Controls
Step 4 – Apply Cybersecurity Controls
The Protect function encapsulated within the NIST CSF necessitates the effective implementation of cybersecurity controls to safeguard the organization’s critical assets. This encompasses the establishment of meticulous policies and procedures governing access control, data protection, and security training. Furthermore, it entails the seamless integration of technical controls such as firewalls, intrusion detection systems, and encryption.
Step 5 - Establish Detection and Response Capabilities
Step 5 – Establish Detection and Response Capabilities
Within the NIST CSF framework, the Detect and Respond functions assume paramount importance by facilitating the implementation of cutting-edge capabilities geared towards the swift and effective detection and response to cybersecurity incidents. This encompasses the continuous monitoring of systems and networks, the establishment of robust incident response procedures, and the regular conduct of training and exercises to fortify the organization’s defensive capabilities.
Step 6 - Create a Resilient Cybersecurity Recovery Plan
Step 6 – Create a Resilient Cybersecurity Recovery Plan
The Recover function incorporated within the NIST CSF orchestrates the development and implementation of a meticulous plan aimed at swiftly recovering from the aftermath of cybersecurity incidents. This comprehensive plan encompasses the establishment of backup and recovery procedures, the creation of a streamlined communication plan, and the regular execution of testing and exercises to ensure preparedness.
Step 7 - Monitor and Evaluate the Effectiveness
Step 7 – Monitor and Evaluate the Effectiveness
Once the cybersecurity program has been instituted, the indispensable task of diligently monitoring and assessing its efficacy unfolds. This includes conducting regular risk assessments to identify evolving threats, actively monitoring for incidents, and meticulously tracking performance metrics to gauge the program’s effectiveness.
Step 8 - Continuous Improvement
Step 8 – Continuous Improvement
The very essence of the NIST CSF lies in its inherent capacity for perpetual improvement. Through the regular review of the cybersecurity program, any necessary updates can be promptly implemented to address emerging threats, vulnerabilities, and evolving changes within the organization’s operational landscape.