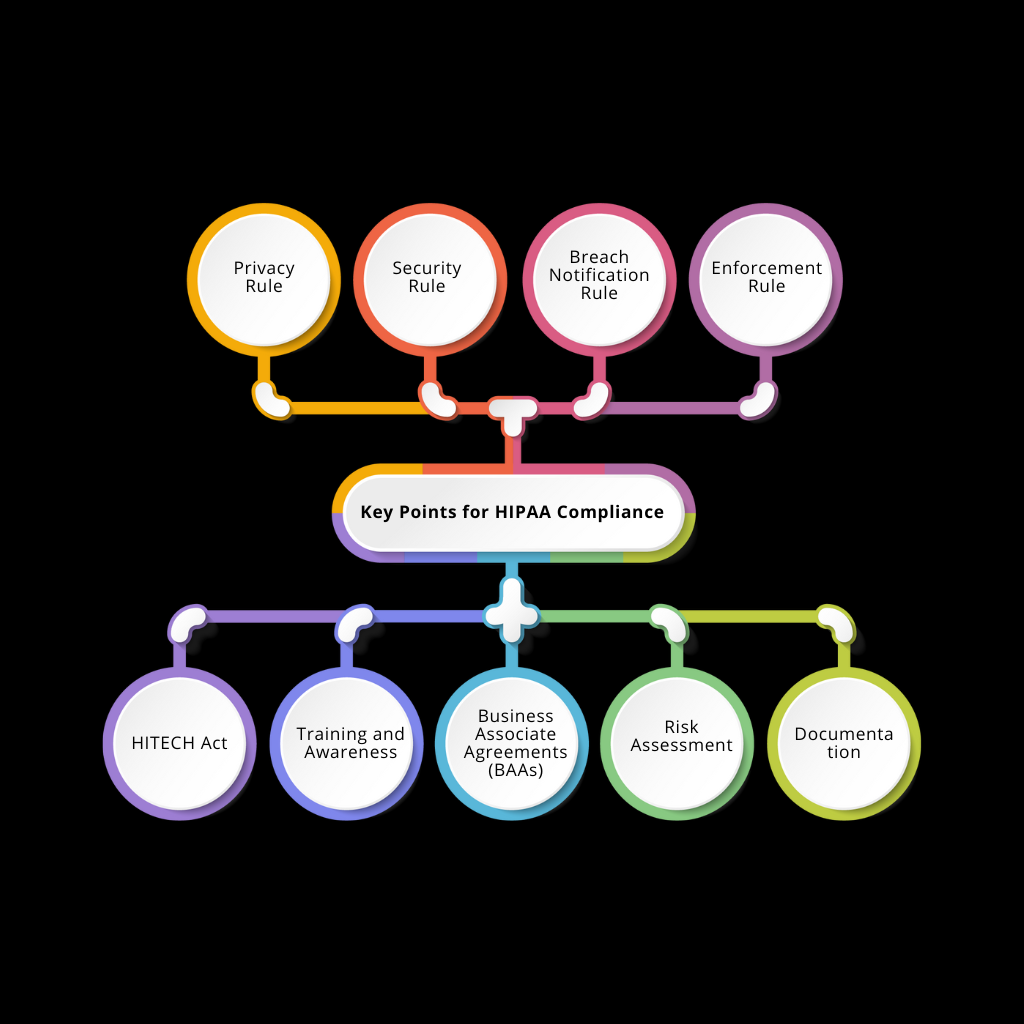
Step 1 - In-depth Gap Analysis
Step 2 - Risk Assessment and Management
Step 3 - Customized Policies and Procedures
Step 4 - Employee Training and Awareness
Step 5 - Robust Access Controls
Step 6 - Secure Infrastructure and Data Storage
Step 7 - Proactive Incident Detection
Step 8 - Rapid Response and Recovery
Step 1 - In-depth Gap Analysis
Step 1 – In-depth Gap Analysis
Our expert team conducts a meticulous assessment to identify existing gaps and vulnerabilities in your organization’s HIPAA compliance framework. We thoroughly evaluate your policies, procedures, technical controls, and employee training to provide a comprehensive overview of your compliance posture.
Step 2 - Risk Assessment and Management
Step 2 – Risk Assessment and Management
We perform a comprehensive risk assessment, identifying potential threats and vulnerabilities that could compromise PHI security. Based on the findings, we develop a tailored risk management plan, prioritizing mitigation strategies to minimize risk exposure and enhance compliance readiness.
Step 3 - Customized Policies and Procedures
Step 3 – Customized Policies and Procedures
We work closely with your organization to develop comprehensive and tailored policies and procedures that align with HIPAA regulations. Our team ensures that all necessary privacy, security, and breach notification policies are in place, reflecting the specific needs of your organization and keeping you up to date with evolving regulatory requirements.
Step 4 - Employee Training and Awareness
Step 4 – Employee Training and Awareness
We conduct engaging and informative training sessions for your staff, focusing on HIPAA compliance obligations, security best practices, and the importance of safeguarding PHI. By promoting a culture of compliance and instilling a strong sense of responsibility, we help your employees become your organization’s first line of defense against data breaches.
Step 5 - Robust Access Controls
Step 5 – Robust Access Controls
We help you implement advanced access controls, including role-based authentication, user activity monitoring, and encryption, to ensure that only authorized individuals can access PHI.
Step 6 - Secure Infrastructure and Data Storage
Step 6 – Secure Infrastructure and Data Storage
Our experts assist in building a secure IT infrastructure, leveraging state-of-the-art technologies and industry best practices. This includes implementing secure data storage, backup mechanisms, encryption protocols, and regular vulnerability assessments to maintain data integrity and resilience against cyber threats.
Step 7 - Proactive Incident Detection
Step 7 – Proactive Incident Detection
We deploy advanced monitoring systems and employ real-time threat intelligence to identify potential security incidents and breaches promptly. Our team utilizes robust log analysis and intrusion detection systems to quickly respond to any unauthorized access attempts or suspicious activities.
Step 8 - Rapid Response and Recovery
Step 8 – Rapid Response and Recovery
In the event of a security incident or data breach, we provide immediate response and guidance, minimizing the impact and ensuring compliance with breach notification requirements. Our incident response experts work closely with your organization to contain the breach, restore operations, and implement necessary corrective measures to prevent future occurrences.